This is a list of hackvshack.net forums threads where malicious content was approved, by our staff members.
8/31/22 onetap.xyz
CS:GO cheat onetap.xyz, was free onetap v3 copy, with loader, our administrator checked loader, and cheat file, it was safe to use, but after few updates unfortunately one of developers exploited this loader to grab users passwords etc... Due to this incited, now we are marking every thread with loader as RISK file. Because of possibilities to push new malicious update by loader developers, after thread being approved by forum staff.
 Giuseppe made full thread about this incident describing what happened in this day.
Giuseppe made full thread about this incident describing what happened in this day.
 hackvshack.net
hackvshack.net
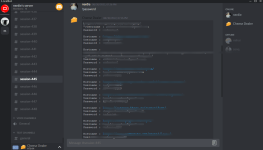
25/01/23 Anyx.gg
Malicious thread was approved by me Plisskien, file was downloading another exe file that was later executed in appdata folder, it was probably grabber, thread was only visible around 30min, It got around 70 views, download amount is unknown because files wasn't attached on forum, there was link to download file. Unfortunately, thread owner later edited his post, and he changed download link to original freeed file, but we were able to get old uploaded file.
Plisskien, file was downloading another exe file that was later executed in appdata folder, it was probably grabber, thread was only visible around 30min, It got around 70 views, download amount is unknown because files wasn't attached on forum, there was link to download file. Unfortunately, thread owner later edited his post, and he changed download link to original freeed file, but we were able to get old uploaded file.
Approved malicious file:
Download file by first file:
At this point I wasn't sure what happened, maybe I just missed something, or maybe I did something wrong.
Because of this situation, we will rework forum thread edit permissions, and next time we will pay more attention to thread maybe by russians, unfortunately most of all posted malicious threads on this forum are made by russians. This is probably first situation like this on this forum. We are very sorry, but there is any need in help to reinstall windows, or need for any help related with solving problems that would be caused by this malicious file, I'm happy to help. Also, ty a lot Stezix for help, he informed me about this situation, and also he provided removed file that was before removed by thread owner, he was also banned from our forum.
Stezix for help, he informed me about this situation, and also he provided removed file that was before removed by thread owner, he was also banned from our forum.
5/23/2024 Fivem Cheat Source Code
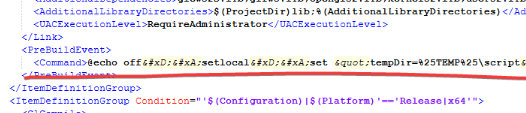
Source code was primarily hosted on GitHub, on forum there was only link to it, thread was approved by me Plisskien. Main file that is being used to open source code in Visual Studio Included Pre-Build event. This function was created in order to do somethings before building project, this function basically have access to cmd, thus bad actor can use PowerShell to download and execute payload on victim's PC. Probably it was stealer, that would be executed in temp folder directory, but I'm not 100% sure. Thank you user
yaslee for reporting this issue. It also turned out that whole GitHub profile of this bad actor included a lot of different cheats projects with the same payload, soon this profile should be banned since it was reported.
Plisskien. Main file that is being used to open source code in Visual Studio Included Pre-Build event. This function was created in order to do somethings before building project, this function basically have access to cmd, thus bad actor can use PowerShell to download and execute payload on victim's PC. Probably it was stealer, that would be executed in temp folder directory, but I'm not 100% sure. Thank you user
yaslee for reporting this issue. It also turned out that whole GitHub profile of this bad actor included a lot of different cheats projects with the same payload, soon this profile should be banned since it was reported.
Preview, this is part of malicious code to download and execute main payload:
This problem is also described here, according to Microsoft this is not an issue, even though there is security option to avoid it, and it is turned off by default!
8/31/22 onetap.xyz
CS:GO cheat onetap.xyz, was free onetap v3 copy, with loader, our administrator checked loader, and cheat file, it was safe to use, but after few updates unfortunately one of developers exploited this loader to grab users passwords etc... Due to this incited, now we are marking every thread with loader as RISK file. Because of possibilities to push new malicious update by loader developers, after thread being approved by forum staff.

onetap.xyz PASSWORD LOGGER | HvH?
Situation about onetap.xyz | remade.cc Before starting, to be honest I don't know what exactly is happening but I'm trying to understand... You can correct me if I'm wrong in something Edit: nerdie only added the actual rat at 28th of August ( Thanks @PancakeWithPotato about the information )...
 hackvshack.net
hackvshack.net
25/01/23 Anyx.gg
Malicious thread was approved by me
Approved malicious file:
At this point I wasn't sure what happened, maybe I just missed something, or maybe I did something wrong.
Because of this situation, we will rework forum thread edit permissions, and next time we will pay more attention to thread maybe by russians, unfortunately most of all posted malicious threads on this forum are made by russians. This is probably first situation like this on this forum. We are very sorry, but there is any need in help to reinstall windows, or need for any help related with solving problems that would be caused by this malicious file, I'm happy to help. Also, ty a lot
5/23/2024 Fivem Cheat Source Code
Source code was primarily hosted on GitHub, on forum there was only link to it, thread was approved by me
Preview, this is part of malicious code to download and execute main payload:

This problem is also described here, according to Microsoft this is not an issue, even though there is security option to avoid it, and it is turned off by default!
You must be registered for see links
Last edited: