Average Enjoyer
- User ID
- 34690
- Messages
- 59
- Reactions
- 1,462
- Level
- 39
Hello dear hackvshack users, in this short tutorial I will give you some indications if a DLL is safe to use or not.
Okay let's start:
This tutorial contains packed and non packed dll files!
Let's use IDA to check further for imports to see which ones it uses
Let's take a non packed dll file at first:
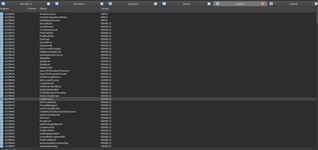
now we are at the import's page from IDA let's take a look if it uses any import's that might indicate to a infected DLL
As we can see it uses ShellExecute what can this be used for? well everything you can execute with an shell is also possible in c++:
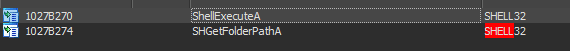
So let's take why exactly the import is been used for:
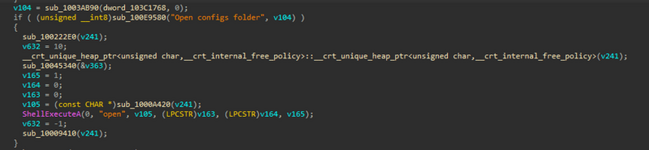
as we can see it is been used for opening the config directory so this is not been used for malicious use
Let's take a deeper look:

as we can see again a possible malicious import again let's take a look at what exactly this shit does:
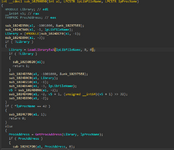
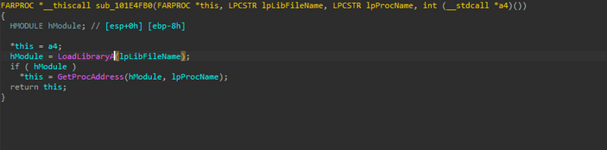
as we can see this is yet again nothing for malicious use again
2 possible malicious import's which is not been used for suspicious use. also keep in mind for looking for URLDownloadToFile in this specific file there is no such use.
We could also search for strings for anything malicious for an example CURL or any other lib that might grab your token or whatever
so after taking a look at all this shit above let's see if we can catch anything in the entry point of the DLL
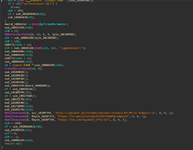
as we can see yet again ShellExecute is been used again, which use? well to open useless websites on injection
Let's take a look at an actual packed DLL file
as we can use this file as been virtualized well does not matter in our case to check if the file is malicious or not.
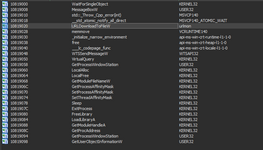
as taken a look at the import's we can see the use of URLDownloadToFile so what exactly can happen? well it might download only font's because the cheat coder does not know how to use
Because this file is virtualized we cannot see what exactly it downloads so how can we actually find it what it downloads? either you can dump the dll in it's entrypoint and work your way with ida (this is not a go to way tbh) or use a debugger in a VM to see what exactly it downloads.
in this case, it was a malicious DLL and I used x64 to debug the process
so the URLDownloadToFile was used to download a rat and execute itself upon injection
So let's pack it up what can you do if a file is packed? well dump that shit and take a look at it it won't magically remove the virtualized file
there are mannny ways to execute malicious code so let's do a few rules when dealing with DLL's
1. Stop been stupid, don't download DLL's from untrusted sources. HackVSHack is a perfect place for your safe use, we check every file that is been uploaded and always check the prefixes for each thread, If you would like to know more about this system check out this page: Files status.
2. Downloaded DLL and you are not sure whenever it's safe to use? if you have no knowledge in reversing abit you should delete the DLL and don't inject at all for your own safety
3. Upload your DLL to virustotal and take a look at the report's and deeper looks there is also a Community tab to see if anyone has taken a look at it and if it's a known malicious HASH
End up Information:
Just because it's a DLL you can do basically everything such as an exe there are no limit's on what you can do to harm your windows by executing a DLL. Use your healthy human brain to figure out if you REALLY want to inject a random dll you received from any youtube video / random forum / discord
Okay let's start:
This tutorial contains packed and non packed dll files!
Let's use IDA to check further for imports to see which ones it uses
Let's take a non packed dll file at first:

now we are at the import's page from IDA let's take a look if it uses any import's that might indicate to a infected DLL
As we can see it uses ShellExecute what can this be used for? well everything you can execute with an shell is also possible in c++:

So let's take why exactly the import is been used for:

as we can see it is been used for opening the config directory so this is not been used for malicious use
Let's take a deeper look:
as we can see again a possible malicious import again let's take a look at what exactly this shit does:


as we can see this is yet again nothing for malicious use again
2 possible malicious import's which is not been used for suspicious use. also keep in mind for looking for URLDownloadToFile in this specific file there is no such use.
We could also search for strings for anything malicious for an example CURL or any other lib that might grab your token or whatever
so after taking a look at all this shit above let's see if we can catch anything in the entry point of the DLL

as we can see yet again ShellExecute is been used again, which use? well to open useless websites on injection
Let's take a look at an actual packed DLL file

as we can use this file as been virtualized well does not matter in our case to check if the file is malicious or not.

as taken a look at the import's we can see the use of URLDownloadToFile so what exactly can happen? well it might download only font's because the cheat coder does not know how to use
You must be registered for see links
Because this file is virtualized we cannot see what exactly it downloads so how can we actually find it what it downloads? either you can dump the dll in it's entrypoint and work your way with ida (this is not a go to way tbh) or use a debugger in a VM to see what exactly it downloads.
in this case, it was a malicious DLL and I used x64 to debug the process
so the URLDownloadToFile was used to download a rat and execute itself upon injection
Code:
Address=43B51B31
Disassembly=push sorryhack (1).43B54318
String Address=43B54318
String=L"https://download852.mediafire.com/hqdsdni4laig/ktrmetcom0z8sxu/*removed"So let's pack it up what can you do if a file is packed? well dump that shit and take a look at it it won't magically remove the virtualized file
there are mannny ways to execute malicious code so let's do a few rules when dealing with DLL's
1. Stop been stupid, don't download DLL's from untrusted sources. HackVSHack is a perfect place for your safe use, we check every file that is been uploaded and always check the prefixes for each thread, If you would like to know more about this system check out this page: Files status.
2. Downloaded DLL and you are not sure whenever it's safe to use? if you have no knowledge in reversing abit you should delete the DLL and don't inject at all for your own safety
3. Upload your DLL to virustotal and take a look at the report's and deeper looks there is also a Community tab to see if anyone has taken a look at it and if it's a known malicious HASH
End up Information:
Just because it's a DLL you can do basically everything such as an exe there are no limit's on what you can do to harm your windows by executing a DLL. Use your healthy human brain to figure out if you REALLY want to inject a random dll you received from any youtube video / random forum / discord