- User ID
- 34690
- Messages
- 59
- Reactions
- 1,413
- Level
- 39
Hello dear hackvshack users, in this short tutorial I will tell you how to bypass any hwid protected dll especially avoz (which most pasters use in legacy lol)
Wrote this on 5AM bare with any grammer or anything else I will edit later if I don't forget it
Okay let's start:
Okay so first we obtain the dll which is hwid protected and check if that shit is packed or not > it's not? we can use IDA to continue > it's packed? use x64 for this purpose
Upon Information:
I will use legacy.codes for the freeing purpose
Okay we open that shit in ida what now? let's jump directly to the entry point of the dll and check it out on first view
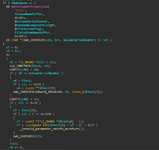
as seen in the pseudocode it checks for hardcoded names and hwid numbers > if we match one of them it will let you inject and show you the specified user within the matched hwid:
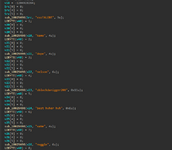
now here the memes begin:
as we can see this especially is the magic avoz hwid checker. so how exactly can smoke this secure hwid checking?
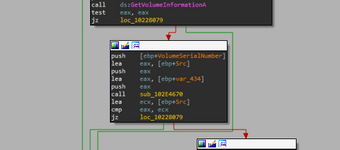
A: We can indeed just spoof our magic GetVolumeInformation how? take a look at this UC Thread:
B: We jump to the right address!
So since B is the best option we will continue on route B
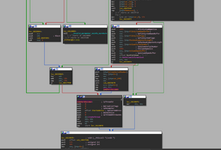
Taking a look at the graph view:
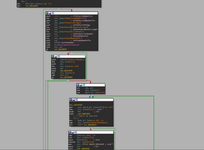
We can exactly see what in the paste it does. what we can do now to skip this premium hwid checking? first let's go to the initialization of the cheat
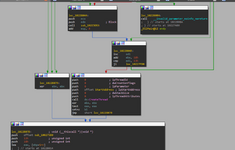
now that's what we want right? of course that's were it starts to load the cheat so let's rename it so we can jump right to it!
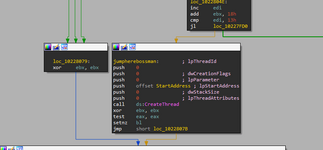
there we go we renamed the function and can now use it to jump right to the function we just renamed!
let's use loc_10228079 to jump to our "jumpherebossman"
there we go! let's apply the patches and start to inject our premium software!
now look at that! we successfully freeed a hwid protected dll!
End up information:
please stop using this non sense hwid avoz protection, I hope with this thread you guys realize how easy it is to bypass such an check and put more effort on the actual security.
aya if you find this useful and used this information to free superior cheat's let me know!
Wrote this on 5AM bare with any grammer or anything else I will edit later if I don't forget it
Okay let's start:
Okay so first we obtain the dll which is hwid protected and check if that shit is packed or not > it's not? we can use IDA to continue > it's packed? use x64 for this purpose
Upon Information:
I will use legacy.codes for the freeing purpose
Okay we open that shit in ida what now? let's jump directly to the entry point of the dll and check it out on first view
as seen in the pseudocode it checks for hardcoded names and hwid numbers > if we match one of them it will let you inject and show you the specified user within the matched hwid:

now here the memes begin:

as we can see this especially is the magic avoz hwid checker. so how exactly can smoke this secure hwid checking?
A: We can indeed just spoof our magic GetVolumeInformation how? take a look at this UC Thread:
You must be registered for see links
B: We jump to the right address!
So since B is the best option we will continue on route B
Taking a look at the graph view:

We can exactly see what in the paste it does. what we can do now to skip this premium hwid checking? first let's go to the initialization of the cheat

now that's what we want right? of course that's were it starts to load the cheat so let's rename it so we can jump right to it!

there we go we renamed the function and can now use it to jump right to the function we just renamed!

let's use loc_10228079 to jump to our "jumpherebossman"

there we go! let's apply the patches and start to inject our premium software!
now look at that! we successfully freeed a hwid protected dll!

End up information:
please stop using this non sense hwid avoz protection, I hope with this thread you guys realize how easy it is to bypass such an check and put more effort on the actual security.
aya if you find this useful and used this information to free superior cheat's let me know!
Last edited by a moderator: